Behind one of Gmail's lesser-known features lies a potential threat to websites and platforms managers.
Gmail is undoubtedly the leading and most popular provider in the consumer market. Consider that as of April 2022 counted 1.8 billion accounts in use with about 30 percent of global market share coverage.
Having this monstrous number of users, Google had to think about how to avoid as much as possible unintentional mismatches when sending email to Gmail boxes.
DOT(s)
Therefore, in the user name (all to the left of the @) the dots and uppercase characters are not valued, so they can be entered but are not actually valued, as if they did not exist.
The most interesting matter lies behind the use of the dot in the username: try sending an email to your Gmail email by inserting or omitting-anywhere in the username-one or more dots.
For example: osintmatter@gmail.com is the same e-mail as osint.matter@gmaill.com or o.s.i.n.t.m.a.t.t.e.r@gmail.com, you can send and receive e-mail to and from any of these usernames that respond to a unique UUID (unique user identifier) and therefore unique owner.
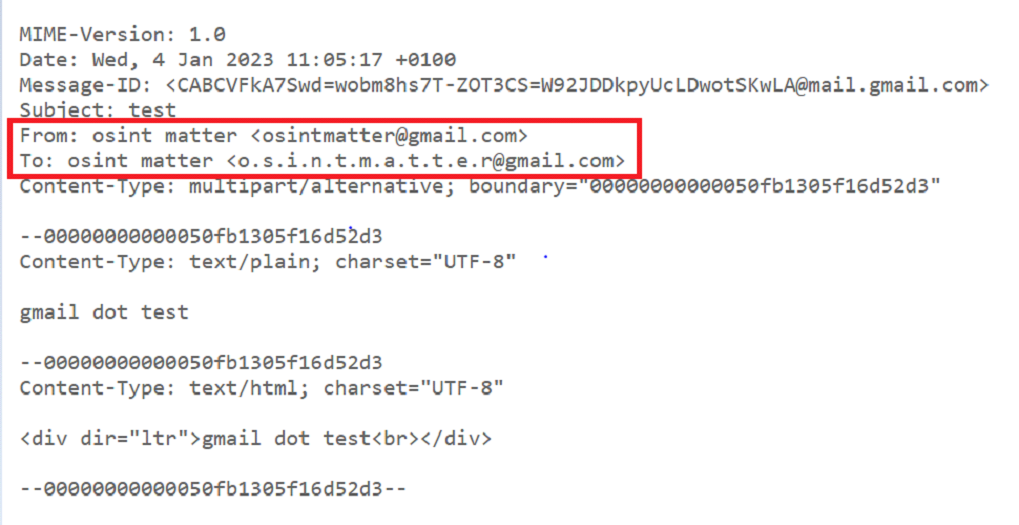
In addition to the dot, Gmail offers other avenues for alias creation: for example, using the “+” character and the domain googlemail.com.
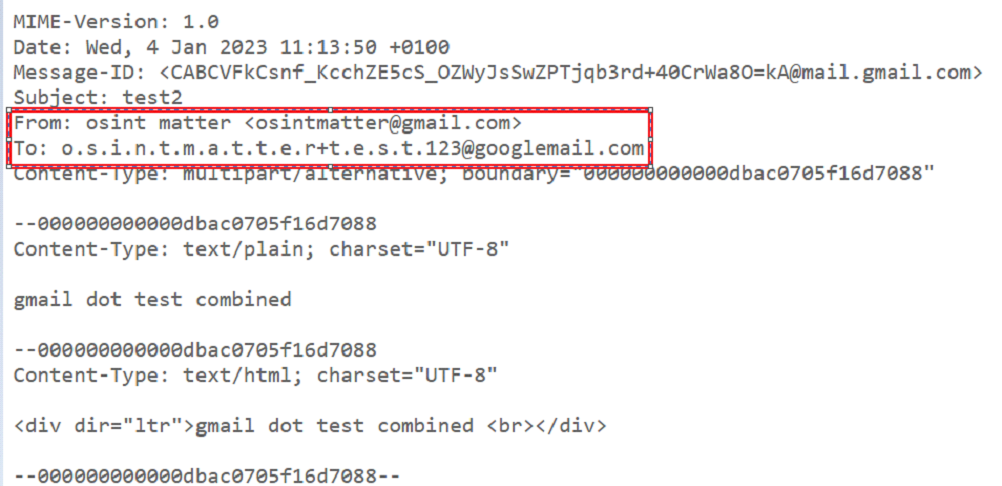
The “+” character allows any additional character in the username to be added after it: osintmatter+test123@Gmail.com always leads back to osintmatter@gmail.com, the domain Googlemail.com on the other hand is the legacy version of Gmail and can still be used instead of Gmail.com.Of course, the three techniques presented can be combined, generating an infinite number of aliases e.g.: o.s.i.n.t.m.a.t.e.r+t. e. s. t.1.2.3@googlemail.com = osintmatter@gmail.com.
The Alias abuse
If on the Google side the inclusion or omission of dots leads back to a single mailbox, the same cannot be said for most online services: here. The user osint.matter@gmail.com is not the same as osintmatter@gmail.com and does not lead back to a single UUID.
Here comes the interesting part: online services that base their user DB on email keys are vulnerable to possible exploits and abuses based on this very seemingly innocuous technique.
The most frequent abuse scenario is bonus-hunting/abusing that is, when operational schemes are used to abuse a bonus offered by an online service. Take, for example, new user registration events via referral codes or welcome bonuses. Companies want to attract new customers through welcome bonuses in the form of in-app usable credit or various discounts. Similarly, it is important for an online service to ensure the spread of its brand through peer-to-peer mechanisms; that is, customers who bring their contacts to register in exchange for a commission recognition for each new user registered through their referral code.
Many online sites, in order to facilitate the user experience, tend to decrease the steps required for onboarding as much as possible: for example, they may require the entry of a mobile number at a stage after registration or make it optional or conditional. By conditional we mean the situation where a new account is created from a device with a fingerprint already known to the back-end systems of the service, or from an account on which there is already a number registered.
For these sites/apps/services, the various aliases generated from a single Gmail e-mail are perceived as unique new accounts with all the attributes and possible benefit provided.
Gmail aliases’s power
The phenomenon of bonus abusing/hunting described is actually ancient and it is certainly not only this technique that makes it possible; however, it makes the process itself incredibly easier and more manageable.
Let’s see why:
• Registering new e-mail addresses is an effort that is not always easy. Imagine having to go through the process of registering an e-mail x times, generating and remembering numerous personal details that are entered as mandatory, jotting down passwords, and hoping not to end up in the increasingly common anti-bot control mechanisms of mail providers. This element should not be underestimated as it is becoming increasingly common to implement controls to prevent the mass generation of e-mail addresses from the same device/IP/useragent.
With the use of Gmail aliasing techniques, all this effort is reduced to zero: no new e-mail registration required, a single password, and no risk of being blocked or branded as an at-risk user.
• Each e-mail provider conducts mailbox access monitoring with the aim of optimizing server storage and eliminating dormant or unused accounts.
This activity is conducted by scripts that monitor the last logged access and, when a given timeframe expires, proceed with account deletion.
For a bonus-hunter, this means conducting scheduled “maintenance” activities of accounts generated for a given pattern of abuse on an online platform.
This maintenance activity is not required using Gmail aliases since access to the UUID of the one account created is continuous.
• Since long time there have been temporary e-mail services that allow you to receive an e-mail at a temporary address that is publicly available online. This option might seem the most effective and efficient for the purpose, but it is not so for a few simple reasons:
1. Temporary e-mail services are opened and closed continuously and without notice;
2. Inboxes are public and allow anyone, potentially, to use the e-mail confirmation link to steal the registered account;
3. Bonus hunters hate high volumes of abuse on a service; this is because the more noise generated, the more likely the victim service is to intervene with remediations or change bonus award policies. So “advertising” the sites you want to abuse on these open channels is usually not a best practice
4. The domains used are particularly exotic and are known to be the most advanced anti-abuse monitoring systems. Thus, often the use of these disposable e-mail addresses leads to an immediate user risk flag and often results in the blocking of the registration process.
• Alias generation services have existed for some time; these services provide a domain with a mail server and a given number of username/addresses that can be generated that have as their only configuration the forwarding of all incoming traffic to the chosen recipient.
This solution is good but not perfect because in addition to having a limited number of accounts that can be generated, you are relying on a third party about whom you know little, and, in addition, they use alphanumeric domains with low registration fees that are, however, easily undetectable compared to classic commercial mail services. It is precisely here that we identify one of the most successful elements of the Gmail aliasing technique: the fact of using the most widely used and popular free mail service in the world. A good way to blend into the average user without raising suspicions.
We now understand the scenario and the mechanics of abuse behind what for all intents and purposes is a great feature designed by Google to prevent errors and to enable segmentation of personal e-mail traffic.
Remediations
In closing, we go on to analyze possible remediations that can be applied by operators of online sites and platforms to mitigate not so much the use of Gmail aliases but their misuse.
This premise is due as abusive behavior is where you exploit that feature to obtain new user status multiple times, not the single use of a Gmail alias.
A first solution, also the simplest, involves the use of regular expressions (Regex) for validating e-mails in user registration forms.
For example, one could implement such a regex control in the e-mail entry field:
([^.](?=[^s@]*@g(oogle)?mail.com))
Analyzing the regex point-to-point:
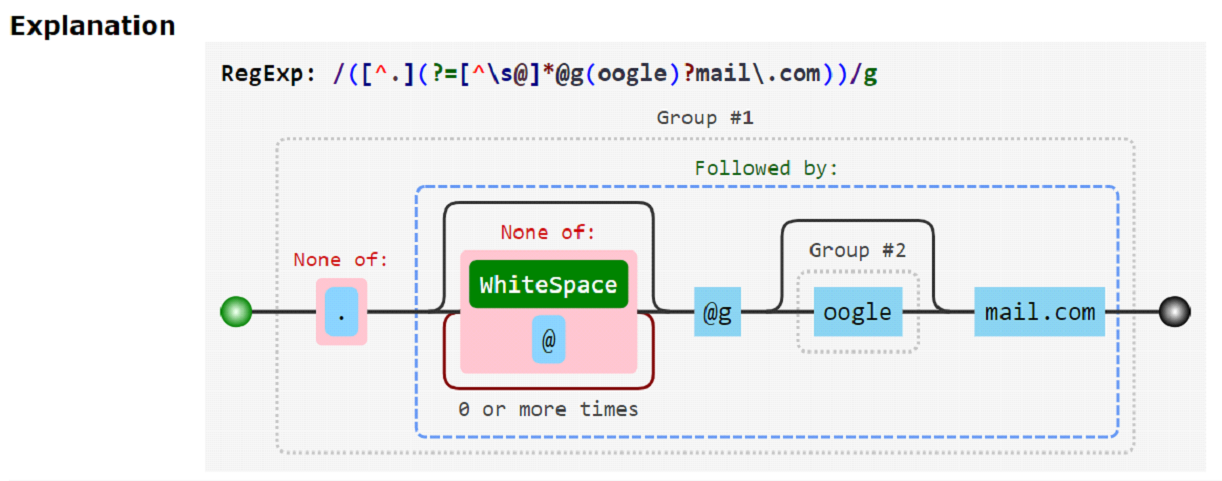
(source: https://extendsclass.com/regex-tester.html )
Basically, not value any dot in the username if the e-mail address contains Gmail or googlemail.com as the domain.
This will only accept a new user using Gmail if their username has not been used before, with or without dots in it.
In addition, it is critical to block usernames that contain special characters within them and in our case Gmail addresses that contain the “+” character.
A third and final technique is Digital Footprint analysis of e-mails during user registration.
To explain what is meant by Digital Footprint, I borrow the definition given by seon.io, one of the world’s leading online anti-fraud services:
“the term refers to the information – the ”footprint“ – we each leave behind as we spend time on the Internet. This is sometimes thought of as, and called, a ”digital shadow“ that a user casts, knowingly or not.
This ranges from registered accounts on various websites and services to our social media accounts and public posts, to upvotes or downvotes on reviews, and so on — including content on all sorts of digital platforms, from ads to forum comments.
These traces we leave online amass over time as we use the web, throughout our lives. And, with 4.55 billion social media users today (58.8% of the global population), there is a lot of such information out there.”
As we have said, to the world outside Google, osintmatter@gmail.com and osint.matter@gmail.com are two separate and independent digital identities. We can use this fact to our advantage by using free services such as GHunt: https://github.com/mxrch/GHunt, freemium tools such as Epieos: https://epieos.com/, or paid ones such as the previously mentioned seon.io to deeply analyze the digital footprint of each e-mail address. Those who abuse the Gmail alias technique generally use each alias for single uses or at least for a few online registrations. It then becomes quite easy to recognize the original account versus its digital clones, just by analyzing the number and type of associated registrations.
You can try a quick free test at https://epieos.com/ by first entering your own Gmail address in current use and then comparing the results with the same address with one or more dots entered in the username before the @: the history of registrations and activities turns out to be totally different and unique.
Just as I was using the few days of “relaxation” to write this short article, it occurred to me that it would be useful to write a tool to help site and platform managers in cleaning up abusive Gmail accounts from their databases.
I then also used those last energies to publish: GDOT, a simple 100% python script that automatically detects google e-mails that use one or more of the techniques described in this article.
You just install the tool locally, import the list of e-mail addresses to be analyzed into a target file, and that’s it: in one click you will find the abusive accounts and can kick them out of your systems!
